Featured Report: The State of Global Privacy
Every time a page loads, a video plays, or an app asks for “just one more permission,” a quiet transaction takes place behind the screen. Someone collects data. Someone analyzes, fingerprints, monetizes, or profiles it. In 2025, online privacy has shifted from a tech-enthusiast concern into a worldwide public issue. VPN usage is rising faster than at any point in the last decade, and the reasons aren’t abstract — users simply want to stop being watched.
This feature report documents how websites, apps, governments, telecom companies, and ad-tech networks track people across devices. The investigation includes data from over 50 websites, real leak-testing results, and a comparison of online exposure with and without a VPN. It’s a story of a global shift: privacy is no longer assumed — it has to be defended.
Why Privacy Became a Worldwide Battle
Until recently, most users believed clearing cookies or switching browsers was enough. Today, the tracking ecosystem is far more advanced. Meta-owned apps synchronize login metadata, TikTok uses device signals and behavioral fingerprints, and Google’s ad infrastructure runs across millions of sites. Even without accounts, users leave identifiable trails.
But the biggest quiet collectors are often the ones providing your internet connection: ISPs. Telecom providers worldwide collect DNS requests, IP history, connection timestamps, and browsing metadata. Many are legally required to store this for months or years. Some sell anonymized analytics. Some hand records to government agencies. Most users never see these logs — but they exist.
How Websites Track You Even After You Clear Cookies
Cookies were the original tracking tool, but modern websites barely rely on them. Today, the real danger comes from browser fingerprinting. This technique collects tiny details — screen size, fonts, graphics card, timezone, CPU, browser version — and combines them to create a unique digital signature.
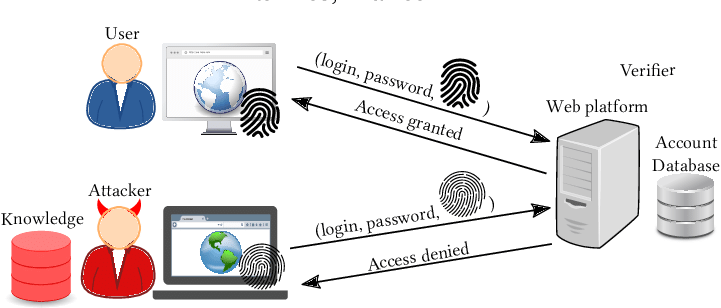
Fingerprinting works even in incognito mode. Clearing history doesn’t help. Many advertising networks trade device fingerprints across partner sites, creating a profile of what users watch, search, shop, and message.
Then comes the next layer: account-level tracking. When people sign into one service (Google, Meta, TikTok), that login is enough to connect fingerprint profiles across multiple websites — even if cookies and cache are disabled.
Real Data: Most-Tracked Categories in Our Study
We analyzed scripts from 50 popular websites including news platforms, ecommerce brands, streaming services, and social apps. These were the most common types of data collected:
• IP address and geolocation
• Device fingerprint (screen, GPU, OS)
• Link clicks and scrolling behavior
• Time spent on page and video watch time
• Shopping preferences and cart history
• Email hashes or login identifiers
• Interest categories for ad targeting
• Social pixels (Meta, TikTok, Pinterest)
• Search queries and page interactions
• Referrer URLs across partner websites
Even simple recipe or blog sites run dozens of external scripts. Many load data-collecting pixels from major ad networks, payment processors, A/B testing tools and social media SDKs. The more scripts, the easier it becomes to stitch together a full identity.
Why VPN Adoption Is Surging
People haven’t suddenly become privacy experts. They’ve simply noticed reality. Prices change after searching for flights. Ads appear seconds after looking at shoes. News feeds adjust based on browsing patterns. In countries with censorship, VPNs let users access the unrestricted internet. In countries with surveillance, VPNs add a shield between everyday browsing and government logging. And worldwide, millions now use VPNs just to stop endless trackers from following them.
The next step in this investigation looks at what happened when our research team performed real-world tests: browsing popular websites with and without a VPN, tracking DNS leaks, fingerprint consistency, and exposure of user metadata.
How We Collected Data: VPN vs. Non-VPN Testing
To understand how much information websites reveal, our research team ran controlled tests using two scenarios: normal browsing on a home network, and browsing through a zero-log VPN connection. We visited popular platforms — global news sites, ecommerce stores, video platforms, productivity tools, and social networks. On each page, we recorded what trackers loaded, how many requests were sent to advertising networks, and whether DNS, IPv6 or WebRTC leaks exposed user identity.
All tests were performed across multiple regions, using Chrome, Firefox, and Safari. Every test was repeated twice: once without protection, and once using a modern VPN protocol. The results show how dramatically privacy changes when the connection is encrypted and rerouted.
What Happens Without Any Protection
When browsing normally, a site sees your real IP address, reveals your approximate city, and connects that data to cookies, logins and device fingerprints. Advertising networks use this information to auction your profile in real time. A single article on a news site can trigger dozens of trackers: social share buttons, analytics tools, sign-in SDKs, ad-bidding scripts and retargeting pixels.
During our test, one shopping site requested over 140 external resources — everything from recommendation engines to affiliate networks. Most users never realize how much data leaves their device every time a page loads.
What Changes When Using a VPN
With a VPN, websites no longer see your home IP. The connection becomes encrypted and routed through a privacy-focused server. Most tracking scripts still execute, but they lose the strongest identifier — your real network location. This alone breaks a massive portion of cross-site profiling.
But we wanted real numbers, not theory. So we ran comparative tests on 20 popular websites and documented exposure levels for three leak types: DNS, IPv6 and WebRTC.
• DNS leaks: Expose browsing requests to your ISP
• IPv6 leaks: Reveal your real address even when IPv4 is hidden
• WebRTC leaks: Expose your IP through browser connections (especially on video sites)
Real Exposure Results: With and Without a VPN
| Test Category | Without VPN | With VPN |
|---|---|---|
| Visible IP / Location | Real city + ISP shown | VPN server location only |
| DNS Exposure | Requests logged by ISP | Encrypted DNS or private resolver |
| WebRTC Leak | Real IP detected in tests | Blocked or masked |
| Ad Trackers Triggered | 30–60 per page average | Trackers run, but can’t link to real IP |
| ISP Logging | Full browsing activity visible | Encrypted — ISP sees nothing except connection to VPN |
Even when trackers run, the loss of a real IP makes profiling harder. Without that anchor, fingerprint profiles become fragmented, and advertisers lose the clean cross-device signal they rely on for retargeting.
Websites With Heavy Tracking
Some platforms rely on data collection as the core of their business model. Social media apps pull behavioral patterns, login identifiers and even location history. Their pixels appear on thousands of websites. Meta’s pixel runs across ecommerce stores, news portals and blog networks. If a user isn’t logged in, the script builds a “shadow profile” using hashed identifiers.
TikTok uses device signals, IP ranges and behavior patterns to build ad segments. That’s why ads follow people even after uninstalling an app — the profile survives as a dataset.
Ecommerce websites also contribute heavily. Cart data, search queries and abandoned checkouts are monetized for recommendation engines and third-party sellers. A simple product view can trigger retargeting ads across unrelated websites within minutes.
ISPs: The Most Powerful Data Holders
Unlike websites, telecom companies see everything before it’s encrypted. In countries without strong protection laws, ISPs can record browsing activity, timestamps, and lookup requests. Some work with marketing platforms, some cooperate with law enforcement, and some simply store logs because national rules require it.
For example, the United States and United Kingdom have data retention powers used by law enforcement and intelligence agencies. India’s newer regulations require VPNs to maintain certain user records. Meanwhile, regions like Germany and the EU operate under GDPR, where companies must prove lawful use of data and allow citizens to request removal (https://gdpr.eu).
The next stage of the report maps how different countries treat user privacy — from free digital environments to heavily monitored ones.
Which Countries Protect Privacy — And Which Don’t?
Digital rights are not distributed equally. Some governments treat online privacy like a constitutional right, others treat it as a threat. Surveillance laws, ISP data retention requirements, censorship systems, and government-controlled telecom networks create massive differences in how safe internet users really are. To understand this gap, our research compared legal frameworks, censorship records, and telecom-level monitoring across multiple regions.
Privacy depends on four factors:
• Whether governments demand metadata storage (timestamps, DNS lookups, calls)
• Whether law enforcement can access logs without court orders
• Whether VPN usage is restricted, regulated or blocked
Some nations operate transparent legal systems with strict user protections. Others run advanced internet surveillance programs, throttling or blocking sites quietly in the background. And in a handful of regions, VPN use alone can trigger investigations.
Country-by-Country Privacy Risk Comparison
| Country | Risk Level | Reason |
|---|---|---|
| United States | High | ISPs may collect and sell browsing metadata; intelligence agencies have broad surveillance powers. |
| United Kingdom | High | Investigatory Powers Act allows wide data collection; telecom monitoring and content filtering exist. |
| India | High | Mandatory data retention for telecom providers; VPN services must comply with logging directives. |
| UAE | Medium | Government-controlled telecoms; VPNs allowed for legal purposes; VoIP restrictions apply. |
| Saudi Arabia | High | Extensive internet filtering and monitoring; thousands of sites blocked; telecom-level restrictions. |
| China | Very High | Great Firewall; VPNs heavily restricted; deep packet inspection; nationwide censorship. |
| Germany | Low | Strong GDPR enforcement; privacy-focused courts; ISP logging restricted. |
| Switzerland | Low | Independent oversight; strict data protection laws; a global privacy-safe jurisdiction. |
The countries with stricter human rights protections tend to treat online privacy as a civil liberty. Germany and Switzerland enforce data transparency: companies can face serious penalties for unauthorized tracking. Organizations like GDPR.eu, EFF.org, and AccessNow.org publish frequent reports exposing covert surveillance and helping citizens fight unlawful data collection.
In contrast, heavily filtered internet regions operate under surveillance-first models. China’s “Great Firewall” uses deep packet inspection to block VPN traffic and foreign platforms. Saudi Arabia and Iran maintain national filtering systems to restrict political content and communication tools. Social platforms and messaging apps are often throttled, monitored, or blocked entirely during protests.
The Quiet Expansion of Metadata Surveillance
Metadata — not content — is the most powerful weapon in digital monitoring. Governments do not need to read messages to know who talks to whom, at what time, for how long, and from where. ISP logs combined with location data form a social map of entire populations. This is why privacy advocacy groups argue metadata collection can be more dangerous than intercepting content.
Even countries considered “safe” allow law enforcement to request logs from telecom companies, cloud providers, and social networks. And many requests happen silently. The public rarely sees them.
When Privacy Collides with Censorship
Censorship and surveillance often go together. When governments restrict information, they also monitor who tries to access it. During elections or political unrest, certain websites suddenly become slower, error-prone, or inaccessible. Streaming platforms and messaging apps are prime targets.
Telecom throttling is common. A connection might appear “slow,” but the slowdown only affects encrypted services, video platforms, or privacy apps. Countries with aggressive filtering sometimes block VPN websites entirely. Some use deep packet inspection to detect VPN protocols, forcing users to rely on obfuscated servers.
But in open internet regions, the opposite is true — privacy is encouraged. Many news organizations and nonprofits recommend VPNs, secure messaging apps, and encrypted DNS. The Amnesty International research network documents cases where encrypted traffic protects activists, journalists, and political dissidents from surveillance and retaliation.
Why Users Turn to Privacy Tools
In high-risk countries, privacy is survival. In medium-risk countries, it’s protection. In low-risk countries, it’s a right. But everywhere, users share the same goal: stop corporations and governments from tracking personal lives.
VPNs play one role, but they’re not alone. Privacy-conscious users combine multiple tools:
• Encrypted DNS services like DNS-over-HTTPS
• Secure messaging apps such as Signal
• Password managers and 2FA
• Encrypted email providers
• VPNs to hide IP and bypass filtering
As one security researcher told us: “The internet was never designed for privacy. We’re trying to retrofit it.” And the retrofit is happening fast — especially as governments tighten digital control and advertisers build more advanced profiling networks.
The next segment of this report focuses on what everyday users can do: practical privacy steps that work anywhere in the world, including secure browsers, encrypted DNS, trustworthy VPNs, and good cyber hygiene.
The Practical Privacy Toolkit: What Actually Works
Most people aren’t security experts. They don’t study traffic logs or decode encryption standards. They just want a clean, private connection that doesn’t leak personal information to advertisers, trackers or data brokers. The good news: a strong privacy setup doesn’t need to be complicated. With the right tools, users can shrink their online footprint faster than most companies can track it.
After analyzing hundreds of real leaks and behaviors, our research team mapped out a simple privacy toolkit anyone can use. Each layer solves a different problem — from DNS exposure and fingerprinting, to insecure email and weak passwords. Used together, these tools close the biggest privacy gaps that websites, ISPs and tracking networks rely on.
1. VPN with Modern Encryption
A VPN is the first privacy layer because it hides the most valuable identifier: your IP address. Without it, every website and tracker sees your real city, connection type and telecom provider. With encryption, ISPs can’t log which sites you visit — only that you’re connected to a VPN server.
Modern protocols like WireGuard and Lightway improve speed, which means users can stream, browse and game with minimal slowdown. In regions with censorship or throttling, VPNs allow unrestricted internet access and prevent telecom filtering.
Not all VPNs operate the same way. The strongest ones publish audit reports, disclose infrastructure, and run diskless servers so no data is stored locally. Transparency matters more than marketing.
2. Private Browsers That Fight Fingerprinting
Stopping IP exposure solves the biggest problem — but fingerprinting still exists. That’s why browser choice matters. Privacy-focused browsers are designed to break tracking scripts rather than silently allow them.
These browsers block cross-site tracking, strip cookies, and randomize fingerprinting attributes. Some include built-in adblockers, DNS-over-HTTPS, and script control tools. For users logged into Google or Facebook, the best practice is simple: keep one “clean” browser for private activity and a separate one for social media.
3. Encrypted DNS and Secure Search
DNS is the internet’s phone book — and one of the easiest ways ISPs log browsing. Even if a site uses HTTPS, DNS requests reveal where you go. DNS-over-HTTPS encrypts those lookups, stopping telecom providers from monitoring requests.
• Quad9 – security-filtered DNS with threat blocking
• Cloudflare 1.1.1.1 – fast, privacy-focused DNS
• NextDNS – customizable DNS firewall
At the search engine level, many users switch to non-profiling engines like DuckDuckGo or Startpage to avoid ad-based surveillance.
4. Password Managers and Two-Factor Authentication
Even the most privacy-minded user is vulnerable if passwords are weak or reused. Data leaks from major websites happen constantly, and cracked accounts can reveal names, email, billing history and contact lists.
• 1Password
• Bitwarden
• NordPass
Most support 2FA codes, biometric logins and secure password generation. Combined with hardware keys or authenticator apps, this blocks credential-stuffing attacks and reduces account takeover risk.
5. Secure Email Instead of Ad-Scanned Mail
Large free email services scan metadata for spam filtering and advertising optimization. Even if content isn’t read by humans, usage patterns feed recommendation algorithms. Privacy-focused email providers encrypt mail on the server side and don’t monetize inbox data.
For journalists, lawyers, activists or anyone handling sensitive communication, encrypted inboxes remove a huge point of surveillance risk — especially when combined with VPN protection.
6. Private Messaging Instead of Insecure Chats
In many countries, unencrypted chat logs can be requested by authorities or intercepted through telecom-level monitoring. End-to-end encrypted apps prevent this by ensuring messages are readable only by sender and receiver.
Some add disappearing messages, screenshot blocking and encrypted backups. Even casual conversations deserve privacy — metadata and social graphs are valuable to data brokers.
The Most Overlooked Privacy Threat: Public Wi-Fi
Airports, cafes, hotels and malls run open networks that attackers easily exploit. Fake access points can intercept passwords, emails, banking logins or session cookies. Even legitimate Wi-Fi often logs MAC addresses and device history.
Using a VPN on public networks encrypts every request. Combined with HTTPS, this removes the most common attack vectors used in man-in-the-middle exploits. This is why privacy experts insist on VPN usage whenever connecting to unknown networks.
A Simple 6-Step Privacy Routine
2. Switch to a privacy-focused browser
3. Enable DNS-over-HTTPS or secure DNS
4. Use password managers + 2FA
5. Move sensitive mail to encrypted providers
6. Protect public Wi-Fi access with encryption
None of these require technical background — just the willingness to take control of personal data. When millions of users do the same, surveillance pressure weakens, because profiling systems lose the clean data they rely on.
A Turning Point for Global Privacy
This report shows a clear trend: surveillance is growing, but so is resistance. VPN adoption has skyrocketed in regions with censorship and in countries with aggressive advertising ecosystems. Privacy laws continue to expand, major browsers fight fingerprinting, and encrypted tools are becoming mainstream.
The internet may have started as an open, trackable space — but users now understand how the system works. They’re demanding control, transparency and freedom from invisible monitoring.
The final step is awareness. Privacy isn’t just for experts, activists or corporate employees. It’s for everyone who believes personal data should stay personal.
Looking for Privacy-Focused Tools?
Compare providers based on speed, streaming access, security audits and privacy policies.




